Troitsky Breach Analysis
This article covers the Troitsky Breach Analysis method. A breach is an opening in the cylindrical shell of the stack that compromises its structural integrity. This is usually either a rectangular ducting connection or a cylindrical pipe nozzle penetrating the stack shell. Previously we have written an article called “Life is a Breach” which outlined the method of analyzing breach using section properties. The section properties method was used in MecaStack up until v5506, at which time we offered another option called “Troitsky”. The Troitsky method is explained in this article, and it is the method we recommend because it is more robust and complete.
After further research into the matter, some corrections have been made in terms of the calculations, which were implemented in v5568 of MecaStack.
What does Troitsky reference?
There is a book titled “Tubular Steel Structures Theory and Design” by M.S. Troitsky. Mr. Troitsky was a Professor of Engineering at Concordia University in Montreal, and this book was originally published in 1982 and the 2nd edition was released in 1990. This book was originally published by “The James F. Lincoln Arc Welding Foundation”, but at the time of this article a visit to their website indicates that it is not currently being offered by them. Performing a Google search there do appear to be some sellers offering used copies of the book. Since it’s not in publication any longer, we have scanned the breach section and included it here for your download.

Selecting Troitsky Breach Analysis:
On the “Breach Reinforcement” screen, you can select the “Troitsky” as the breach design analysis for that breach by selecting the option shown in the image.

Troitsky Breach Analysis Overview:

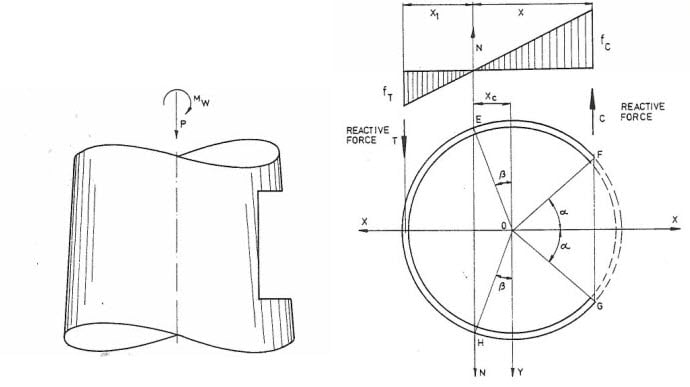
1. Calculate Elastic Neutral Axis:

2. Check Stack Reduced Buckling Capacity
When a hole is cut into the shell, we reduce the buckling capacity of that shell. Let’s assume that a perfect cylinder (one without any cutouts) has a capacity of Pcl. Pcl is the classical compressive load that the perfect cylinder can take before it starts to buckle. Now, lets assume we cut a rectangular hole in the shell. It’s safe to assume that Pcl won’t be it’s limit any longer and that the compressive capacity will be some value less than Pcl. Let’s call this reduced capacity of our cylinder with a cutout, P. Below is Figure 5.23, taken from Troitsky, that shows the relationship of P/Pcl versus rbar. The term rbar is a non-dimensional parameter that takes into account the cylinder geometry and cutout dimensions as follows:
rbar = r / (R*t)^0.5
r = (a+b)/4
a= Width of Opening
b = Height of Opening
R = Radius of the Cylinder
t = Thickness of the cylinder
All units must be the same (i.e. inches, mm, etc..)
Using Figure 5.23 we can find the reduced capacity of the shell section due to the cutout. In the Fig 5.23 there are a couple of curves shown, but in MecaStack we use the lower bound curve to be conservative. After further research into this matter, we have determined a maxium imperfection factor of 0.2 for the P/Pcl value is the best approach. If the use of the figure provides a lower value than 0.2, then we will use the lower value.
In MecaStack we calculate the rbar and then the P/Pcl ratio. Pcl is then calculated as the classical buckling stress (0.6*E*t/R) and multipled by the imperfection ratio of P/Pcl. To get the allowable buckling stress we multiply the classical buckling stress reduced by P/Pcl by the compression factor of safety for the design chosen: (P/Pcl) * (0.6*E*t/R) * FS .

Round Openings:
Traditionally, round openings are referred to as nozzles, and typically these are reinforced using reinforcement pads (repads). When the breach becomes large, then it may be more practical to use vertical and circumferential stiffeners for reinforcement. For this situation, we have added a option on the breach screen to indicate that the opening is round rather than rectangular. This will show the graphics correctly. Also, when the round option is selected, then we follow this Figure 5.25 from Troitsky for the buckling capacity. The remainder of the analysis is the same regardless of whether then opening is round or rectangular.


Is the Shell Buckling Capacity Adequate?
If the reduced shell buckling capacity is GREATER THAN the stress which is placed on the section, then the section is adequate and technically requires no reinforcement. However, it’s always desireable to add reinforcement even if this check passes because it’s only going to improve the buckling capacity if you decide to use reinforcement anyway.
If the reduced shell buckling capacity is LESS THAN the stress being placed on the section, then you definitely have to provide reinforcement of the section. The remaining setps in the flowchart (3 through 6) will now be checked.
3. Verify Breach Area Replaced by Vertical Stiffeners
When the cutout occurs, a certain amount of material is removed. In this check, we make sure that the area removed (the removed area is highlighted in yellow in the image) is completely replaced by the stiffener area.
4. Verify Breach Moment of Inertia Replaced by Vertical Stiffeners
Similar to the area, we also check to make sure that the moment of inertia, which was lost due to the cutout, is completely replaced by the vertical stiffeners.

5. Check Vertical Stiffener for Combined Axial Moment
The axial load and moment is calculated on each vertical stiffener, using the equations in Para 5.7 of Troitsky. The vertical stiffener is treated as a pinned-pinned column for the analysis. Then using the criteria in AISC 360-16 the vertical stiffener is checked for combined axial compression and flexure using the appropriate section of AISC 360-16. The stiffener shape used and configuration determine which sections of AISC are used for the calculations.
These AISC checks are quite involved, and require a lot of calculations. In the case of structural shapes used from AISC, the properties are obtained using the values in the AISC tables. For structural shapes which are included in MecaStack that are taken from other country’s standards (i.e. British, Australian, Brazilian, etc..) the shapes are approximated by using a collection of rectangles. This method should give reasonably accurate results, but it does not take into account fillet radius on corners as found in the actual shape, and so it is an approximate result.

6. Check Circumferential Stiffener for Load Above Opening

The Troitsky Breach Analysis didn’t discuss designing the rings to keep the stack from ovaling, but that seems to be a logical requirement of the ring; therefore, in MecaStack we have added a check that verifies that the moment of inertia of the ring (in bending) is completely replacing the moment of inertia of the cylinder opening that is lost due to the breach cutout.
The Troitsky Breach Analysis assumes that circumferential stiffeners are full rings. There are some examples in industry of the circumferential stiffeners only being above the opening, and not wrapping 360 degrees around the stack. This is discussed briefly in the commentaries of CICIND “Model Code for Steel Chimneys”. They state that when the width of the opning is less than 40% of the stack diameter locally, that it is not necessary to provide a horizontal stiffener extending around the full circumference and a more local arrangement may be used. Vertical reinforcement should be continued above and below the opening to a point where the added stress is insignificant. The code recommends continuing the reinforcement at least 0.5 times the width of the opening.
MecaStack does not have an option to indicate a partial ring reinforcement, but we offer this information as information only. Typically, Meca doesn’t use this type of partial ring reinforcement, we recommend full rings.

Analysis Results
Section Properties & Stiffening Rings
In addition to the Troitsky Breach Analysis, MecaStack is also going to modify the section properties to consider the removal of the cutout and the addition of the vertical stiffeners. The circumferential stiffeners for the breach are not considered in the section properties calculation; however, they are considered as “stiffening” rings for the stack and are considered in all stiffening ring checks that are performed.
Multiple Openings?
There are endless combinations of openings that can occur, and it’s impossible to give a solution that addresses all possibilities. The one thing to remember is that even though MecaStack may graphically show the multiple openings (see corresponding image), it doesn’t mean that it’s properly analyzing multiple openings. The section properties will be modified to include all of the openings, but as shown in this discussion of the Troitsky method, there are a lot more considerations. Each Troitsky Breach Analysis that MecaStack performs, assumes that the breach is the ONLY breach that exists. It does not consider any other breach. The Troitsky method does assume the full area and moment of inertia is replaced with the vertical stiffeners; therefore, basically each breach designed using Troitsky assumes that the reinforcement makes the section equal to or greater than the original perfect cylinder. If you have multiple breach openings and each is designed using Troitsky, then it would seem that each breach should be sufficiently designed to be independent of the other breach; however, it’s not always that simple. The situations can become very complicated and when in doubt refer to experts or perform finite element analysis to validate results.

Example using Troitsky:
This all makes more sense when you apply it to an actual example. To illustrate this, we took “Numerical Example No 1” from Troitsky, and we have simulated the exact same problem using MecaStack. Please refer to the example No 1 in the text, and the PDF of this file can be downloaded here. Please note that in RED we have added comments in a couple of places where more explanation is required. Here you can download a PDF of the comparable MecaStack Output for the same problem, and the results can be compared. The results are very close, and where they differ we have explained why in the comments of the Troitsky PDF.
Is it Breach or Breech?
This is a question that has puzzled stack designers since the beginning of time, is it Breach or Breech? Lets look at the definition for each according to Dictionary.com:
Breech – The lower, rear part of the trunk of the body. In an ordnance, the rear part of the bore of a gun, especially the opening and associated mechanism that permits insertion of a projectile.
Breach – The act or result of breaking; break or rupture. A gap made in a wall or fortification. To make a breach or opening in.
According to the definitions, it seems that BREACH is the most accurate for the context of an opening in a cylidndrical shell; however, I have been using breech to describe this situation for my entire career. The book “Tubular Steel Structures” by Troitsky uses the term breech, and ASME STS-1 uses breech. Consulting with colleages they have stated that they believe that the industry has used breech and breach interchangeably, so that either is acceptable.
At the end of the day, we at Meca have decided that breach is more consistent with the actual situation in which the word is used and so moving forward we will use breach; however, don’t be surprised if you see breech in various locations in our website and software, it’s going to take a while to locate and update all references.
